Just recently got the requirement that user passwords should follow the password security policy of the client. Oracle EBS delivers a number of password policies which may fullfill the need in your organization but to make passwords more secure you have to extend the policies.
Of course it's possible to implement Oracle Access Manager combined with Oracle Internet Directory to hook in to Active Directory but that combination will not be used (yet :-)) so will also not be discussed in this article.
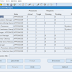
Profile Options
A number of profile options relate to the seeded delivered password policies.
1) the password containts at least one letter AND at least one number
2) the password does not contain the username
3) the password doest not contain any repeating characters

- Signon Password Case: This profile will enable case sensitivity for password. To make it case sensitive it will make passwords more secure because combination of upper and lower characters will be used. When passwords are not case sensitive the entered password by the user will be uppered and validated against the encrypted password stored with the user.
- Signon Password Custom: This profile will provide the name of the custom java class which enables the use of custom, client specific, password policies.
- Signon Password Failure Limit: This profile provides the number of login attempts an user can do. When the number of attempts exceeds this setting the users' account will be blocked.
- Signon Password Hard To Guess: Setting this profile to Yes will provide the following password policies:
1) the password containts at least one letter AND at least one number
2) the password does not contain the username
3) the password doest not contain any repeating characters - Signon Password Length: This profile will give the minimum length of an user password
- Signon Password No Reuse: This profile will provide the number of days an user must wait before reusing an earlier used password.
By enabling the password expiration option on usernames they are enforced to change their password after a certain number of days or after logging in succesfully a number of times. - See more at: http://oracleebsapps.blogspot.in/2011/08/signon-password-policies.html#sthash.l3vgKDu4.dpuf
This profile will enable case sensitivity for password. To make it case sensitive it will make passwords more secure because combination of upper and lower characters will be used. When passwords are not case sensitive the entered password by the user will be uppered and validated against the encrypted password stored with the user.
Signon Password Custom: This profile will provide the name of the custom java class which enables the use of custom, client specific, password policies.
Signon Password Failure Limit: This profile provides the number of login attempts an user can do. When the number of attempts exceeds this setting the users' account will be blocked.
Signon Password Hard To Guess: Setting this profile to Yes will provide the following password policies:
1) the password containts at least one letter AND at least one number
2) the password does not contain the username
3) the password doest not contain any repeating characters
Signon Password Length: This profile will give the minimum length of an user password
Signon Password No Reuse: This profile will provide the number of days an user must wait before reusing an earlier used password.
User setting
By enabling the password expiration option on usernames they are enforced to change their password after a certain number of days or after logging in succesfully a number of times. - See more at: http://oracleebsapps.blogspot.in/2011/08/signon-password-policies.html#sthash.l3vgKDu4.dpuf
User settingBy enabling the password expiration option on usernames they are enforced to change their password after a certain number of days or after logging in succesfully a number of times. - See more at: http://oracleebsapps.blogspot.in/2011/08/signon-password-policies.html#sthash.l3vgKDu4.dpuf
By enabling the password expiration option on usernames they are enforced to change their password after a certain number of days or after logging in succesfully a number of times.

I just recently got the requirement that user passwords should follow
the password security policy of the client. Oracle eBS delivers a number
of password policies which may fullfill the need in your organization
but to make passwords more secure you have to extend the policies.
Of course it's possible to implement Oracle Access Manager combined with Oracle Internet Directory to hook in to Active Directory but that combi will not be used (yet :-)) so will also not be discussed in this article.
Profile Options
A number of profile options relate to the seeded delivered password policies.
By enabling the password expiration option on usernames they are enforced to change their password after a certain number of days or after logging in succesfully a number of times.
- See more at: http://oracleebsapps.blogspot.in/2011/08/signon-password-policies.html#sthash.H2KLDvIr.dpuf
Of course it's possible to implement Oracle Access Manager combined with Oracle Internet Directory to hook in to Active Directory but that combi will not be used (yet :-)) so will also not be discussed in this article.
Profile Options
A number of profile options relate to the seeded delivered password policies.
- Signon Password Case: This profile will enable case sensitivity for password. To make it case sensitive it will make passwords more secure because combination of upper and lower characters will be used. When passwords are not case sensitive the entered password by the user will be uppered and validated against the encrypted password stored with the user.
- Signon Password Custom: This profile will provide the name of the custom java class which enables the use of custom, client specific, password policies.
- Signon Password Failure Limit: This profile provides the number of login attempts an user can do. When the number of attempts exceeds this setting the users' account will be blocked.
- Signon Password Hard To Guess: Setting this profile to Yes will provide the following password policies:
1) the password containts at least one letter AND at least one number
2) the password does not contain the username
3) the password doest not contain any repeating characters - Signon Password Length: This profile will give the minimum length of an user password
- Signon Password No Reuse: This profile will provide the number of days an user must wait before reusing an earlier used password.
By enabling the password expiration option on usernames they are enforced to change their password after a certain number of days or after logging in succesfully a number of times.
- See more at: http://oracleebsapps.blogspot.in/2011/08/signon-password-policies.html#sthash.H2KLDvIr.dpuf